
Phishing – in the modern digital world, you no doubt have an idea of what phishing entails, but do you know where the name comes from?
In the mid-90s, hackers were fast at work targeting America Online (AOL) accounts. Hackers knew most users wouldn’t take the bait from rather obvious email-based “fishing” lures, but they also knew a select few, out of the sea of internet users, would inevitably respond.
The ph spelling in phishing is a throwback to infamous hacker and information security pioneer John Draper (aka, Captain Crunch) whose work exploiting U.S. telephone systems is best identified by the industry standard term: phreaking.
Thus the term phishing was originally coined to describe the sneaky email messages that caused users to inadvertently part with their AOL accounts nearly 30 years ago. Today, the term has exploded to include a broad array of social engineering techniques used to gain access to a target system.
Most phishing messages are still emails. In the past, phishing emails would simply ask for a user to respond with their username and password. More recently, however, phishing emails are much more sophisticated than simply asking for credentials. Messages can contain malware attachments, embed malicious forms to steal sensitive information, as well as contain links to whisk a trusting user off to a dangerous third-party site.
Although phishing isn’t new, it’s a constantly evolving threat and its latest manifestation should be added to your defense team’s watchlist, pronto.
A large organized crime syndicate operating out of Eastern Europe has debuted a new spin on an old technique designed to bypass your enterprise defenses: they send an email requesting a phone call from your users. This syndicate is called the Trickbot Gang.
The Trickbot Gang
Simply listing the aliases of this group and their associated malware would span more than a decade of history and occupy more than three full pages of text. The Trickbot Gang has defrauded banks globally of more than $100 million through direct credential theft facilitated by the Trickbot Trojan. As if that’s not enough, the group is also known to operate multiple forms of point-of-sale malware. Last but not least, Trickbot is also associated with two of the most sophisticated and dangerous forms of ransomware in operation today: Ryuk and Conti.
Describing Trickbot as a cybercrime group is a bit of an understatement. They could more aptly be described as a cybercriminal enterprise, operating much more like a Fortune 500 than a cadre of misfit hacker punks.
Most Prominent Access Technique
Despite all of the various forms of cyber mayhem unleashed by Trickbot over the years, phishing has consistently been the cornerstone of this massive criminal operation. The security community has a name for this latest type of phishing message that solicits an end-user to call the threat actor: BazarCall.
The Latest Evolution of Phishing: BazarCall
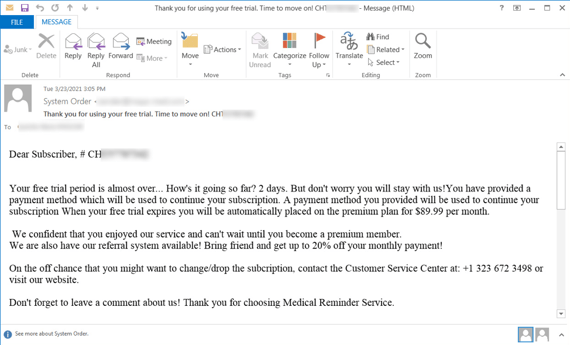
The BazarCall attack works as follows. The user receives an email that urges them to call the actors immediately to cancel a trial before they are automatically charged. Since the email contains no links or attachments, the initial messages are unlikely to be detected as malicious.
Upon calling the number, the user is directed by a live agent to visit a specific site to download a cancellation form. The site prompts the user to enter a customer ID that is contained within the subject of the original email message. If a valid ID is not provided, the agent simply assures the user the trial is canceled and hangs up.
After entering a valid customer ID, the malicious site automatically downloads a malicious Excel file with macro-enabled content – a file with embedded commands. If the threat actor can convince a user to click enable content (macros), malware will be promptly downloaded to the machine. Secondary downloads were originally limited to BazarLoader malware. However, additional payloads have been observed leading to Trickbot, IcedID, Gozi IFSB, and other malware infections.
Banks and credit unions should do everything they can to adopt the latest technologies that enable them to stay secure. Notwithstanding, technology is never perfect. At the end of the day, your users can be your strongest or weakest link. While you may consider yourself an “old hat” in the security realm, don't forget that threat actors are always innovating. Invest the time to educate your users about cybersecurity. Don’t write off phishing attacks as a bygone threat. What once took the form of a fake login page or a malicious attachment could be today's BazarCall.
An example of the BazarCall lure email:
Want to see a BazarCall in action? Check out this video.
Lastly, here are top tips to share with your employees. Stay safe out there.
Stay up to date with the latest people-inspired innovation at Jack Henry.
.svg)

Learn more about people-inspired innovation at Jack Henry.
Who We Serve
What We Offer
Who We Are